As this article shows, the comparison of CEH to Pentest+ is misleading. In a nutshell, you would not compare a cake to flour, as it makes no sense to compare an entire dish to a single ingredient. Ethical hacking on its own is NOT pen-testing.
Penetration testing focuses on the security of the specific area defined for testing. Ethical hacking is a comprehensive term and penetration testing is one of the functions of the ethical hacker.
Perhaps due to the popularity of its name, CEH has been incorrectly perceived to be a penetration testing course. It is not. EC-Council CEH course is a catalyst that can lead a learner to a variety of jobs in information security and not just penetration testing.
In many organizations, ethical hackers are not even involved in penetration testing teams or processes. Across many government organizations, ethical hacking is used to build the foundations of Computer Network Exploitation (CNE) and Computer Network Attack (CNA) Team. While these teams are highly offensive and very specialized, they will never be part of a penetration test. Their tactical cyber skills are highly coveted and take years to develop. In other organizations, Ethical Hackers are used for a wide variety of job functions to augment networks and methods by which tools and protocols communicate. Some are technicians for Intrusion Prevention Teams, SOC II Incident Handlers, Threat Hunters, etc. Ethical hacking indeed has a part in pen-testing, but that is just a piece. Ethical hacking on its own has grown into a very exciting dynamic profession over the past 15 years and truly stands on its own.
If you are looking to compare EC-Council’s pen-testing program to another, you should compare it to ECSA instead.
Ethical Hacking is NOT Penetration Testing!
As the IS/IA profession matures, the core functions of the Information Security professional mature as well. Many companies have dedicated teams to handle the various aspects of cybersecurity, from Network and Sys Admins to Audit teams, SOC teams, Threat analysts, Incident Response and Handling, etc. Due to the scope required to protect systems and their critical role in organizational success, many companies outsource certain elements of their cybersecurity programs to third-party service providers with the proper expertise.
Ethical hacking is a practice. The skills employed by an ethical hacker allow them to practice a continuous assessment cycle of an organization’s security posture by employing the same tools, methods, and techniques of a cybercriminal (malicious hacker). Ethical hackers often have deep knowledge of the organization and its vulnerabilities, as well as its vulnerability management approach. Understanding possible weaknesses, they then utilize the same methods and tools a malicious hacker would use to exploit the weaknesses. This process allows organizations to test systems, vulnerabilities, security measures, policies, etc. to help identify risk, setup countermeasures, deploy defensive resolutions to problems, etc. The very nature of hacking is to use a system in ways it was not intended to be used to produce an outcome not expected by design.
So, what is Penetration Testing?
Penetration testing is a coordinated assessment process, usually performed by a team generally contracted. The organization defines the scope of what is to be tested and reported. The test involves a variety of items, but for the simplicity of explanation, an individual or team under contract would approach a system, assess the entire system for vulnerabilities or weaknesses through a predefined methodological approach, many times, those vulnerabilities are exploited in a controlled manner to identify the risk to the organization. From this point, a pen-tester would prepare a comprehensive report that includes an executive summary, vulnerability classification documents describing the issues in the system tested along with exploitation records showing what threat those vulnerabilities, if exploited, pose to the organization. Paired with an understanding of the business value of the system, exploitation results can help establish a risk score or matrix. With the executive summary, vulnerability classification, and exploitation results, recommended remediation strategies can be documented and shared in detail with key organization stakeholders in the form of a pen-test report.
Penetration tests are valuable for a variety of reasons. The most common are security maturity and risk management. This is a proactive approach many organizations take to identify their own weaknesses before cybercriminals do. Most commonly, however, penetration tests are used for compliance auditing. One example, for instance, is: with a publicly-traded company that is subject to SEC filing, the quarterly and annual financials reported to the SEC must be accompanied by an independent security audit validating the integrity of that companies’ systems. That independent security audit is a penetration test report.
The chart below may further help define some of the differences.

The EC-Council Pen testing Track
As established above, penetration testing, commonly referred to as pen-testing, is a coordinated, contracted, well-defined process that employs a variety of elements from scope identification and agreement, vulnerability assessment and classification, exploitation, documentation, report writing, risk analysis and categorization, and communication. The baseline skills for each of the aforementioned items must be considered to develop these skills in an individual or a team. EC-Council has been in the business of building penetration testing capabilities for companies all over the globe for the last 15 years.
Many consulting firms consider their pen-testing practices as proprietary and offer independent third-party penetration testing as a service in a common consulting engagement. Companies who decide to build this capability in house employ pen-testing as a continuous process for IT/IS Security Management to reduce risk and maintain a superior position with their cybersecurity programs. Once capable teams are assembled, companies can reduce their reliance on third-party assessors and increase the frequency of internal testing and consequently their cybersecurity posture and maturity.
How does this categorization help you?
Whether you are considering building pen-testing capability for an individual or a team, the baseline practical knowledge requirements are the same. Individuals, or collectively as a team, the pen-test process will require a variety of knowledge, skills, and abilities. At EC-Council, we have found many companies are going through the process of trying to transition from having an IT team that supports the business and outsources nearly all elements of cybersecurity, or they some fundamental cyber practice and want to develop and mature their cybersecurity capabilities in-house. Some organizations are looking to develop the practice to provide cybersecurity consulting services;
some have mandated these skills be validated and developed as parts of their team, such is the case with the United States Department of Defense and all contractors that work with them. DoD provides the skills requirement guidance under the DoD Directive 8140 and the new CMMC review processes.
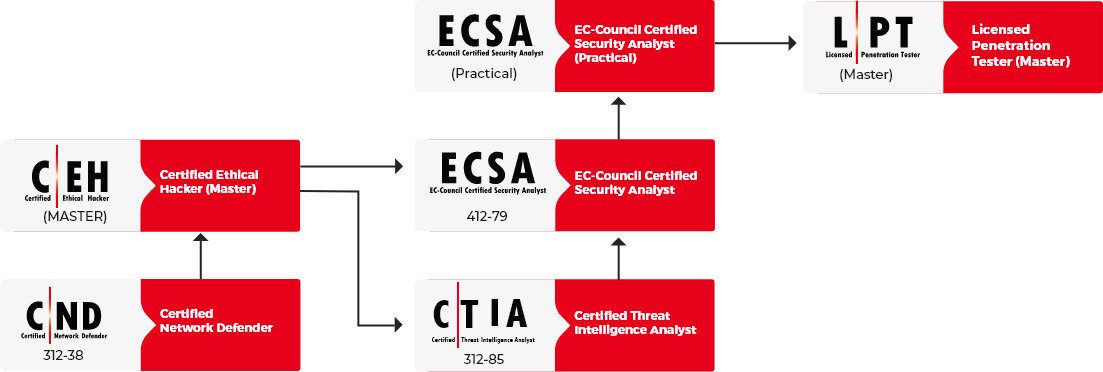
Let’s have a look at how EC-Council develops skills that penetration testers need. We break the core skills down into our Penetration Testing Track focusing on three primary skill areas: Secure Operations, Ethical Hacking, and Security Analysis.
Secure Operations & Network Defense
EC-Council’s Certified Network Defender is really our entry point into the tactical roles for cyber professionals. CND covers the basis of cybersecurity defense. This program covers the operating environment for cybersecurity, covering how information systems function, what role technology plays in these systems and how hackers exploit these systems. Securely provisioning, operating, and maintaining IT systems is paramount to the success of any program. When weaknesses are found in the pen-testing process, it is often this line of defense that is tasked with deploying countermeasures and monitoring systems to ensure risk is remediated.
Ethical Hacking
The second core skill consideration is ethical hacking, covered by our Certified Ethical Hacker program, individuals learn the tricks of the trade in hacking. The word ‘ethical’ in ethical hacking indicates hacking practices; many of the same divisive techniques used by malicious cybercriminals are used intentionally by paid professionals to test systems in the same way hackers exploit them. Unearthing weaknesses and exploiting them with the intention to measure and remediate. Ethical hacking is offensive by nature, professionals proactively seek and hack into their own organization (or organizations they are under contract with) with the sole purpose of identifying, qualifying, measuring, and documenting vulnerabilities and risk the company or organization has. Ethical hacking as a practice often focuses on a single system or vulnerability. Commonly referred to as Red Teaming, Cybersecurity teams will intentionally exploit a weakness, such as brute-forcing a password, performing SQL injection on a web form to break into a web server or database server, exploit a zero-day in an unpatched operating system to establish command-line access to a machine or environment.
Simply put, Ethical Hackers are the professionals you call when you need to break in or want to see how hackers may break into your own organization. They are professionals at attacking systems from a variety of different angles to gain access and maintain it.
Security Analysis
The third core skill consideration in establishing pen-testing capability is security analysis. EC-Council’s ECSA or Certified Security Analyst program dives deep into the penetration testing and security analysis process. In the previous two focus areas, network defense and ethical hacking, we established secure network provisioning and operation, as well as the skills needed to break in through the 5 phases of ethical hacking. With ECSA, those skills all get tied together. ECSA teaches how to take the attack vectors, vulnerability classification systems, contracting process, and report writing to summate everything into actionable intelligence. This is the report building process of penetration testing. ECSA candidates will apply the skills learned in CEH to uncover vulnerabilities, exploit them, document and classify them, and roll them up into a robust, comprehensive pen-test report. Together, the ECSA will focus on the entire organization’s security posture developing analysis methods to uncover problems across the entire org, then employ the skills of ethical hacking to dive into each vulnerability found and attack the target systems known as exploitation to derive a picture of risk. The comprehensive reporting process sets an effective communication standard to demystify complex cybersecurity challenges into a risk matrix that key stakeholders in the organization (non-cybersecurity professionals) can understand and act on for the benefit of the organization.
Credentialing, Knowledge vs Skill Assessments
A standing discussion in the training and certification world is the role of practicals or performance-based assessment. A key example of this is a driving test. Students are trained on the rules of the road, given a written assessment to ensure they understand the rules, then taken out with a driving instructor to demonstrate they can physically operate the vehicle and follow the rules learned in their training. Once the student may ace the written exam, then plow right into the parking cones when trying to park the vehicle safely. The only way to overcome this is to spend time in the car, learn how the vehicle turns, accelerates, and stops. Eventually, the student masters operating the vehicle and passes the practical portion.
With more complex topics like cybersecurity, it has historically been difficult to measure skills (the driving experience). Traditionally multiple-choice questions (MCQ’s) have been the most prevalent method of testing knowledge. Certification bodies like EC-Council have added difficulty to MCQ’s by creating performance-based questions requiring students to compute answers or use frameworks to derive answers. Others have incorporated simulations into their exams, adding software to provide some performance measures in a controlled setting. At EC-Council, we didn’t find any of these methods effective enough to test skills. They do a great job of assessing knowledge, and there is a place for that, but for those looking to truly measure skills, we have to turn to a more complex method of assessment using real cyber environments, not simulators or interactive animations. To this end, EC-Council has developed what we call Master Certification Tracks. Master tracks combine the MCQ assessment with a comprehensive Practical conducted on an actual Cyber Range. The range provided by EC-Council’s iLabs division provides the student on-demand access to data center environments where virtual machines are used in combination with curated networks, attack files, evidence files, network traffic, vulnerable targets such as websites, operating systems, routers, etc. Students are tasked to deploy the knowledge they gained in class and measured on their MCQ exam in a real datacenter based network. Successfully demonstrating skills unlocks secure files, flags in the system that are submitted into our scoring network, proving the student successfully accomplished the performance tasks being measured. Candidates who hold Master Certifications have successfully demonstrated their knowledge by passing the MCQ, and successfully demonstrated the application of that knowledge, or skills in a measured practical, live cyber range environment. Simply put, they know how to do it, and have proven they can do it.
CEH Master

ECSA Master

LPT Master













